How to Capture/Analyze Network Activities from Memory
How to Capture/Analyze Network Activities from Memory https://www.windowsscope.com/wp-content/uploads/2016/07/nsblog1-1024x786.jpg 1024 786 WindowsSCOPE WindowsSCOPE https://www.windowsscope.com/wp-content/uploads/2016/07/nsblog1-1024x786.jpg
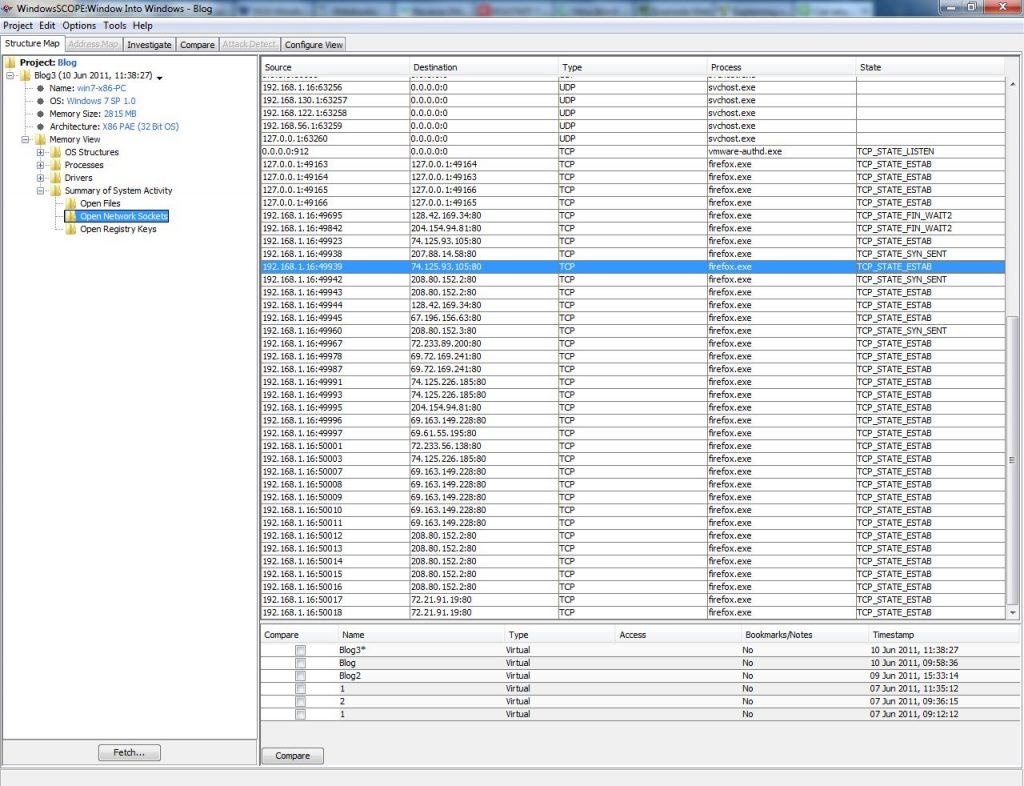
Any network connection can then be examined. For example, take a closer look at the Firefox connection in the example snapshot that has a ‘Destination’ 74.125.93.105:80. This means that the process is accessing the IP Address 74.125.93.105 using Port 80 by means of TCP. In addition to viewing a summary of the network activity, network activity specific to an individual process is also available. For the firefox.exe process being examined, going to Memory View → Processes → firefox.exe → Open Network Sockets will list the network connections for firefox.exe.
A list of commonly used TCP/UDP ports can be found here:
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
Searching through the list of commonly used ports, Port 80 is generally used for Hypertext Transport Protocol (HTTP), or in layman’s terms web browsing. In terms of security, a Firefox process using this port does not seem suspicious. In order to delve further into this open connection, a reverse DNS lookup can be performed using the IP Address listed. This will reveal information about the domain (and in turn, potentially the company/website) with which this connection is established. There are many free reverse DNS lookups available online. The IP Address in this example, 74.125.93.105 is linked to the domain 1e100.net, which is owned by Google. It turns out that Firefox just had a Google service open such as Gmail, Youtube, Search, etc.
In addition to Firefox, which is expected to have an open network connection, there are many other processes that, at first glance, are less likely to have an open connection, and are thus more interesting to examine in detail. In the example snapshot, the Windows process svchost.exe established a connection to the IP Address 65.54.81.46 through Port 80. Using a reverse DNS lookup, the IP Address ends up pointing to msecn.net which is used for updating Windows. Although Svchost.exe is a commonly hijacked process for malicious purposes; it seems in this case, that the network connection is legitimate. WindowsSCOPE can be used to examine any process that is making a network connection in Windows, revealing interesting, and potentially suspicious, information regarding a system’s network connectivity.


